Author: Michael Opdenacker
-
Contributions to Linux 6.19
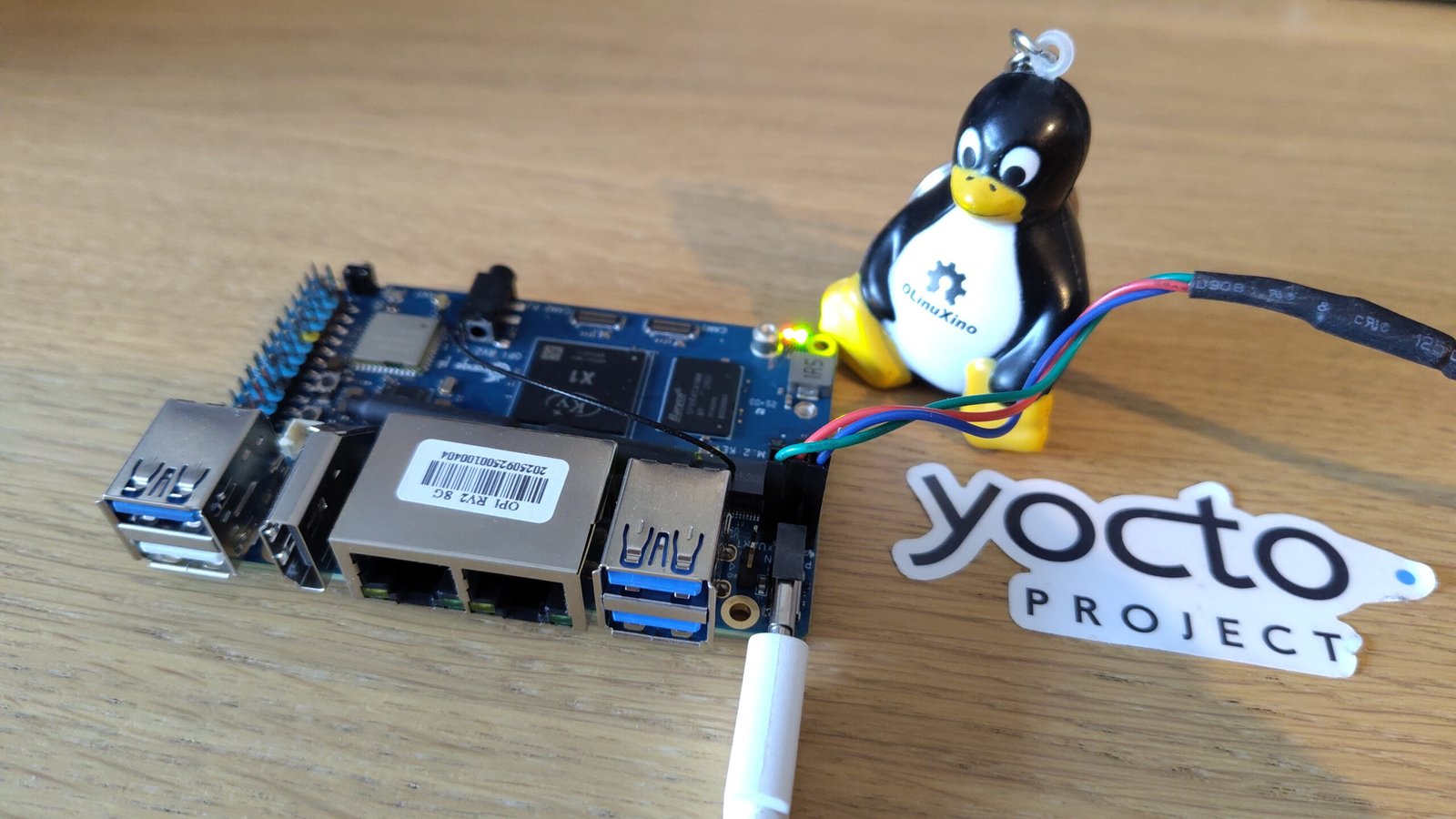
Root Commit’s contributions to Linux 6.19 Linux 6.19 is out with 7 contributions from Root Commit: These are mainly Device Tree contributions to support completely new boards in the Linux kernel, such as Asus Tinker Board 3S (arm64) or Orange Pi R2S (riscv), or to expand support for existing boards, here for Orange Pi 3B…
-

Linux 6.17 is out and already running at Root Commit
Linux 6.17 has just been released, and it’s already running here at Root Commit. The first system it’s been running on is this Toradex Verdin iMX8M Mini SOM (below the heat sink!) on the Dahlia Carrier board. I’m using this board for a medical device project at the moment. Here are my notes for building…
-

Digital hygiene: use USB tethering to connect your laptop
When you are on the go, have you thought about connecting your GNU/Linux PC to the Internet through a USB connection to your phone? A better and safer solution is USB tethering. Your PC uses the Internet connection of your phone through a USB data cable. This is much better in terms of security (nothing…