




Last week, I gave a “Making Yocto Built Images More Secure” presentation at the Embedded Linux Conference in Amsterdam.
The main goal was to share the research I’ve done so far for a customer project, and gather feedback from the audience.
Here are a few highlights:
- Choose well supported versions of Yocto, the Linux kernel and the bootloader.
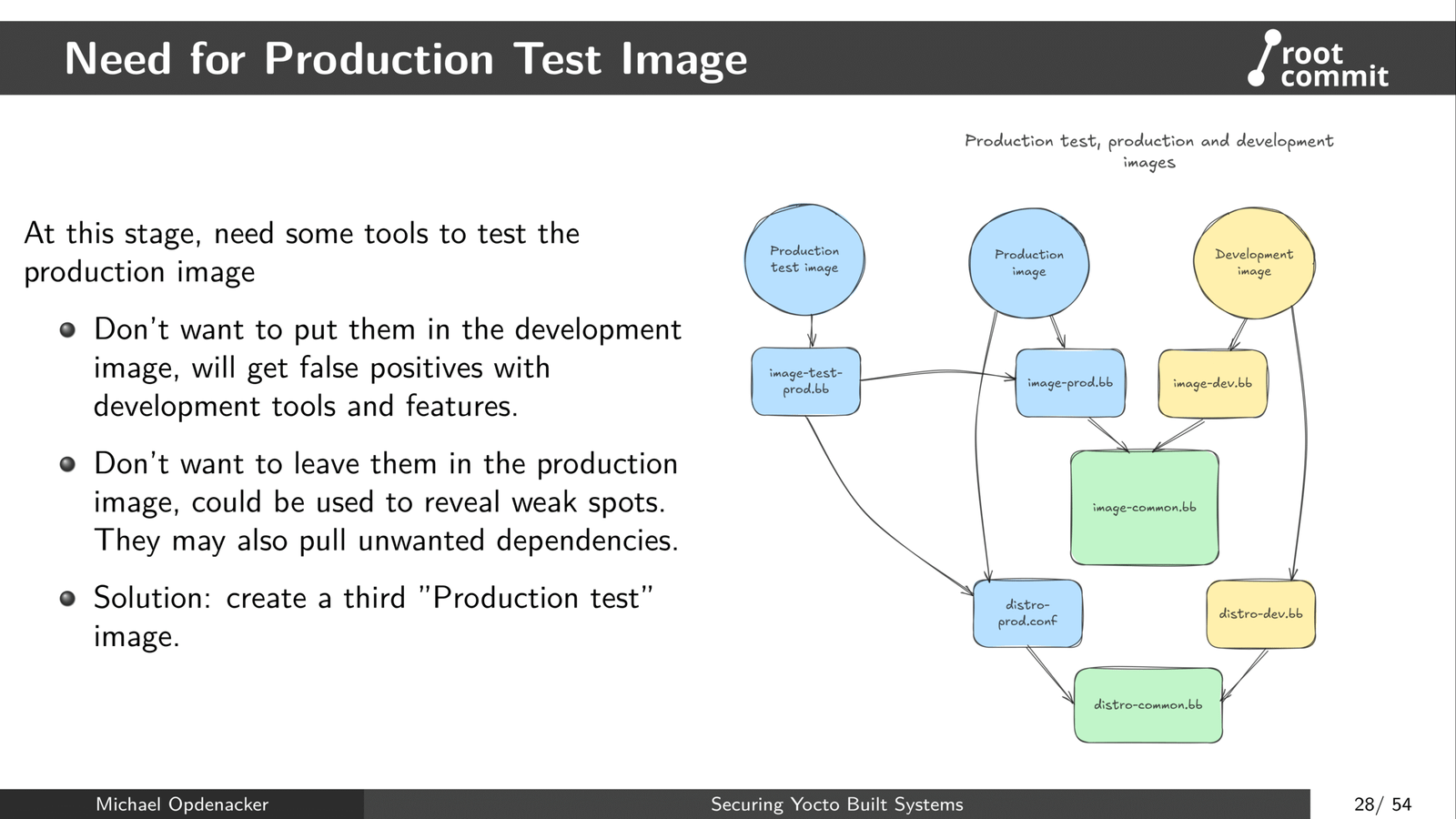
- Define 3 images for your project: developer, production and production testing.
- Remove all unnecessary packages and features.
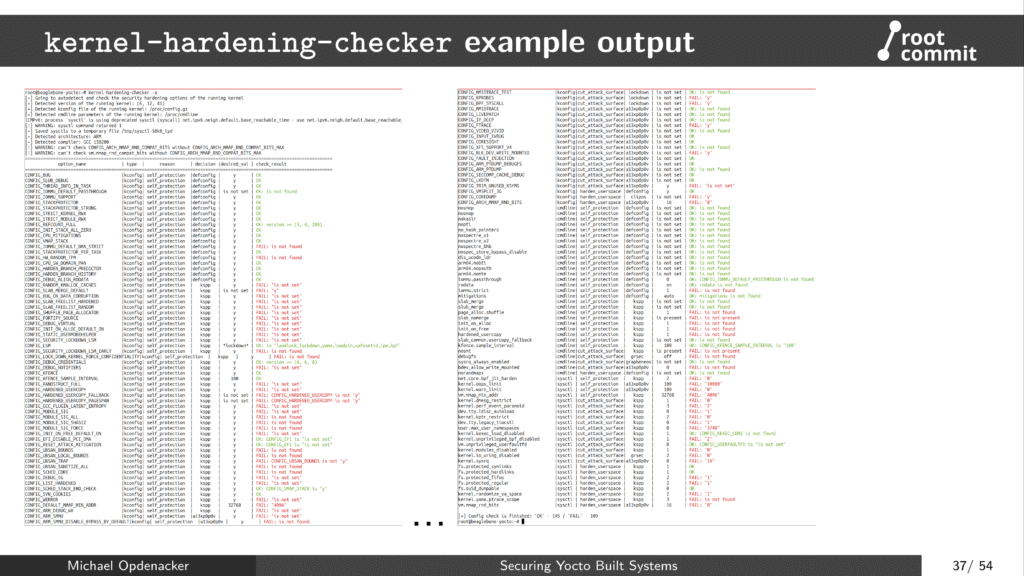
- Use kernel-hardening-checker from Alexander Popov to find opportunities to reduce the attack surface of your kernel.
- Make sure public services are run with limited permissions and resources. That’s easy to enforce with systemd.
- I’m also sharing ways to make passwords unique. Each device should have different passwords.
- Implementing a read-only root filesystem is easy, especially with systemd which works just fine with such a filesystem. If changes have to be done on files on
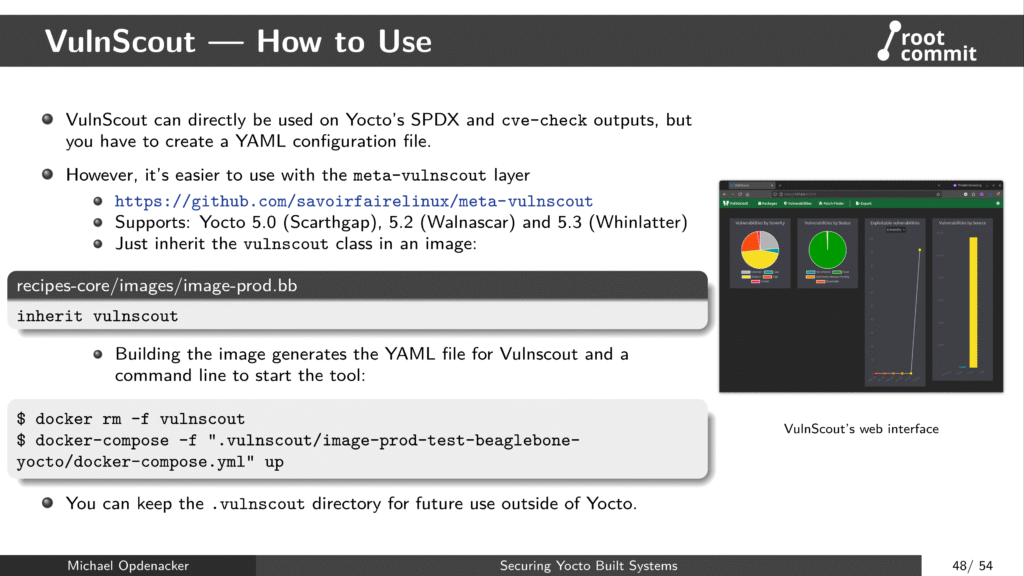
/etc/, use the overlayfs-etc class. - A new tool from SavoirFaireLinux, VulnScout, makes it possible to run vulnerability assessments at any time from Yocto’s SPDX and CVE report
output, without having to run Yocto again. That’s what SPDX was created for, right?
Check out the slides at https://rootcommit.com/pub/conferences/2025/elce/yocto-security/yocto-security.pdf.
In the next weeks, I will publish more specific blog posts about Yocto security. Some of them will feature suggestions I received from the audience, like lynis to scan for weak spots in your userspace stack and in your Linux kernel. This tool was pointed to me by Esa Jääskelä and by another person in the audience.
Here are the blog posts in this series so far:
- Securing Yocto Built Systems overview presentation slides ⬅️
- Yocto Security: Production and Development Images
- Yocto security: Kernel Hardening

